01
Blog
All news, articles and current services for further reading
02
Aktuelle Blogs
All news, articles and current services for further reading
Digital Identity
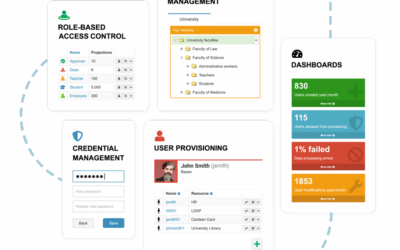
Customer Identity & Access Management enables the clear identification of individuals and the assignment of only the appropriate access rights – in a secure, efficient, and user-friendly manner. Digital identities such as ID Austria represent a modern approach that replaces central data silos and is also accepted by authorities and banks.
Why identity management?
An identity management system is essential for securely and efficiently managing employees within increasingly complex and growing IT landscapes. It enables fast, streamlined processes, enhances IT security, and adapts flexibly to change and business growth.
ID Austria
ID Austria is the successor to the Handy-Signatur, enabling secure digital identification for both public and private sector services since 2022. It supports standard protocols like SAML2 and OpenID Connect and can be seamlessly integrated into existing identity and access management systems.
Open-Source in Digital Identity 2022 - WSO2 Identity Server vs. RedHat Keycloak
Open-source solutions are gaining increasing importance in the field of digital identity, offering flexible alternatives to commercial CIAM platforms. This article compares WSO2 Identity Server and Red Hat Keycloak in terms of features, integration capabilities, and suitability for CIAM requirements.
Midpoint – An Open-Source Identity Governance Platform
MidPoint is a leading open-source IGA platform developed by Evolveum that combines traditional IAM capabilities with compliance and security requirements. The solution is well-suited for complex IT environments – from on-premises to hybrid and cloud deployments.
ID Austria - Login with OpenID Connect
ID Austria is the successor to the Handy-Signatur and enables secure access to digital services. As Austria’s national eID, it is based on the eIDAS regulation and is used for digital identification and access to online public services.
Cybersecurity Under NIS2: A Compliance Burden or a Cybersecurity Lifeline?
Another day, another cybersecurity breach.
You see the headlines, sigh, and move on. "At least it’s not my problem," you think. Until one day, it is.
IAM Expert Summit 2025 – eIDAS 2.0: Digital Identity – Curse or Blessing?
After two successful events, the time has come again: Ventum invites innovators, pioneers and industry experts to its third major summit!
Inspiring Trust Relationship by Securing Digital Identity
Imagine networked objects exchanging information and claiming to improve the universe.